Clients
Clients in Authlink represent applications that request authorization to access protected resources on behalf of Subjects. These applications access Audiences through secure OAuth2 flows. Authlink supports multiple client types to accommodate different application architectures and security requirements.
Client Types
Authlink implements two primary client types based on OAuth2 specifications, each designed for different application scenarios and security capabilities.
Public Clients
Public clients are applications that cannot securely store credentials, typically because their code or storage is accessible to end users.
Characteristics:
- Cannot maintain client credentials securely
- Primarily use Authorization Code flow with PKCE
- Include mobile apps, SPAs, and desktop applications
- Require additional security measures due to exposure risk
Examples:
- Mobile applications (iOS, Android)
- Single-Page Applications (React, Angular, Vue)
- Desktop applications
- Browser-based JavaScript applications
Confidential Clients
Confidential clients are applications that can securely store and protect credentials, typically server-side applications with secure storage capabilities.
Characteristics:
- Can securely store client secrets and certificates
- Support multiple authentication methods
- Include server-side web applications and APIs
- Higher trust level with extended capabilities
Examples:
- Server-side web applications
- Backend APIs and microservices
- Server-to-server integrations
- Trusted system components
Client Identity
Every client in Authlink has multiple identifiers for different purposes:
Client ID
- Public Identifier: Used in OAuth2 flows and token requests
- Unique: Across the entire Authlink instance
- Stable: Remains constant throughout client lifecycle
- OAuth2 Standard: Standard
client_idparameter
Subject ID
- Token Identity: Used as
subclaim when client acts as Subject - Immutable: Never changes once assigned
- Client Credentials: For machine-to-machine scenarios
- Audit Trail: Links client actions to identity
Authentication Methods
Clients authenticate with Authlink using various methods based on their security capabilities and requirements.
Public Client Authentication
Public clients primarily use no authentication (none) since they cannot securely store credentials:
POST /token
Content-Type: application/x-www-form-urlencoded
grant_type=authorization_code&
code=AUTH_CODE&
client_id=public-client-123&
code_verifier=PKCE_VERIFIER&
redirect_uri=app://callbackConfidential Client Authentication
Confidential clients support multiple authentication methods:
Client Secret Basic
POST /token
Authorization: Basic Y2xpZW50X2lkOmNsaWVudF9zZWNyZXQ=
Content-Type: application/x-www-form-urlencoded
grant_type=client_credentials&
scope=api:readClient Secret Post
POST /token
Content-Type: application/x-www-form-urlencoded
grant_type=client_credentials&
client_id=confidential-client&
client_secret=secret&
scope=api:readAuthorization Flows
Authorization Code Flow (Public Clients)
Client Credentials Flow (Confidential Clients)
Multi-tenancy Support
Clients can be associated with specific tenants:
- Tenant Isolation: Clients scoped to specific tenants
- Cross-tenant Access: Controlled scenarios for shared services
- Tenant-specific Configuration: Different settings per tenant
- Resource Restrictions: Access limited to tenant resources
Client Management
Managing clients effectively is crucial for maintaining security and ensuring proper application integration. Authlink provides two primary approaches for client management: the Authlink Portal web interface for administrators and the Portal API for programmatic management.
Portal Management
The Authlink Portal provides a comprehensive web interface for managing clients through an intuitive user experience.
Client Management Interface
The Portal's client management interface allows administrators to:
- Create New Clients: Register public and confidential clients with appropriate configuration
- Update Client Settings: Modify redirect URIs, scopes, and authentication methods
- Manage Credentials: Generate and rotate client secrets for confidential clients
- Configure Flow Settings: Set authorization flows, token lifetimes, and security policies
- Set Custom Properties: Add application-specific metadata and branding
- Monitor Usage: Review client activity, token issuance, and authentication patterns
Portal Access
Access to client management features requires appropriate administrative permissions. Ensure your account has the necessary roles before attempting to manage clients.
Public Client Creation Workflow:
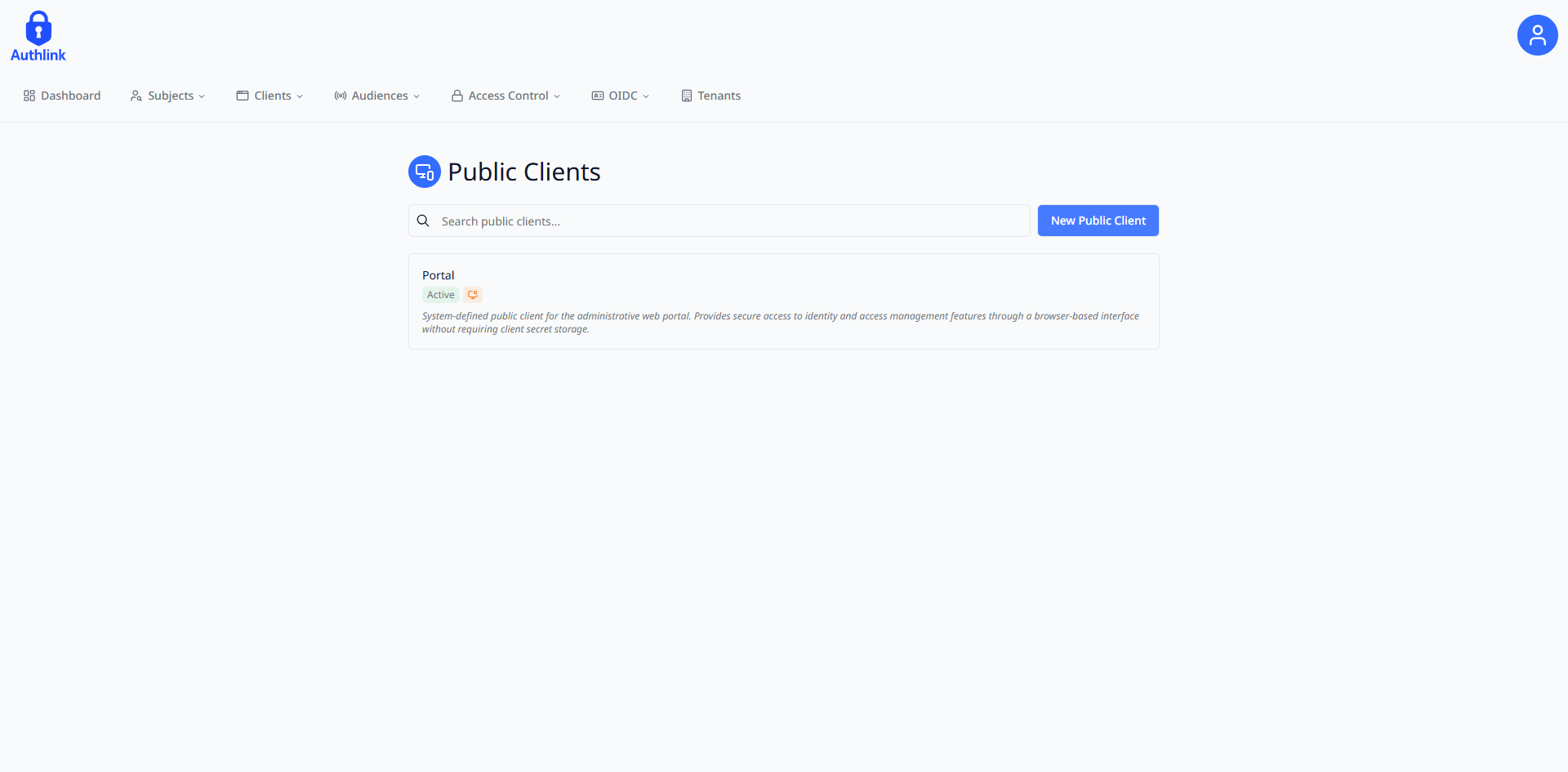 Navigate to https://portal.authlink.co.za/public-clients and click on the "New Public Client" button
Navigate to https://portal.authlink.co.za/public-clients and click on the "New Public Client" button
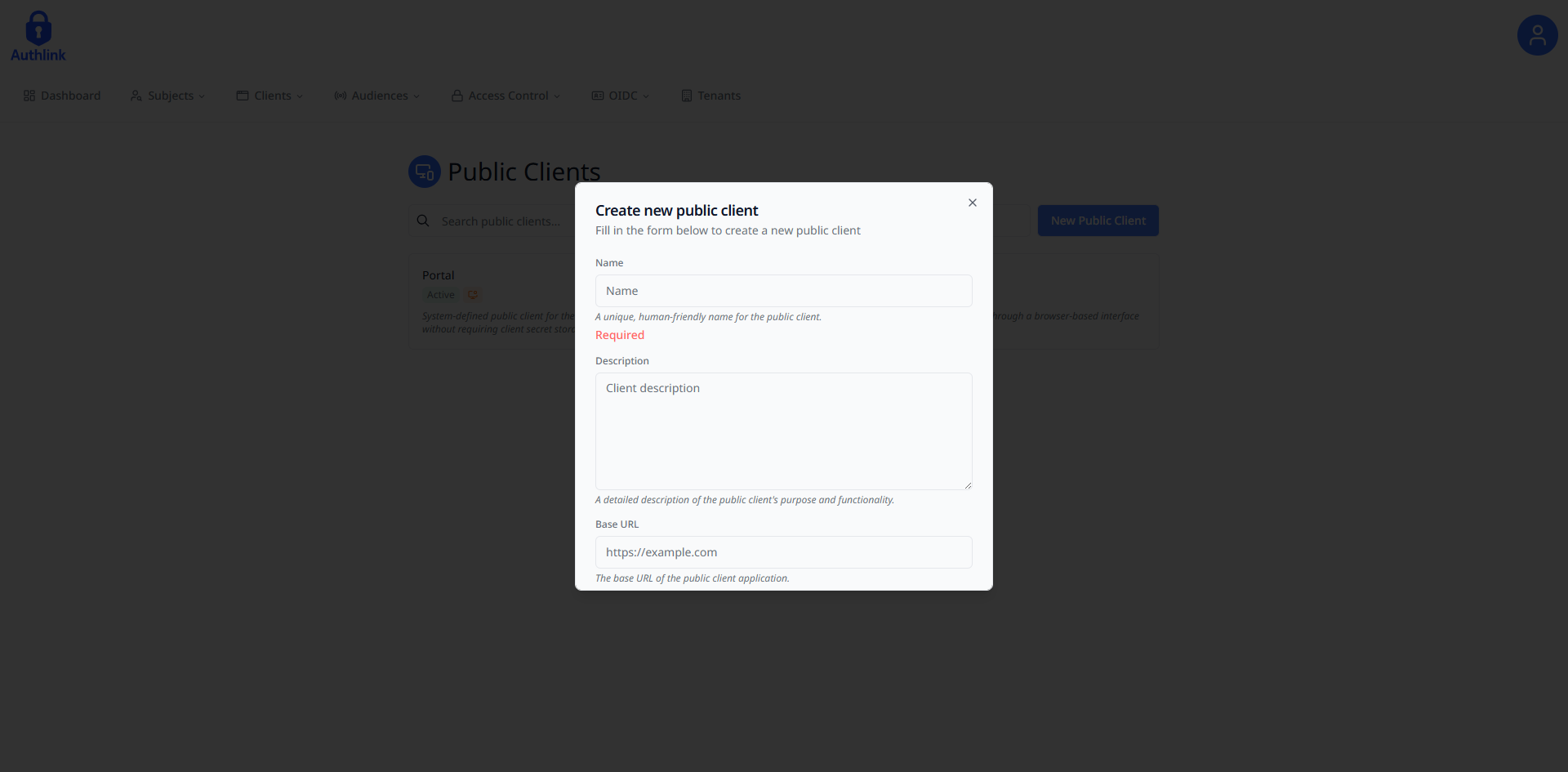 Fill in the required form fields needed to create a public client and submit once finished
Fill in the required form fields needed to create a public client and submit once finished
Confidential Client Creation Workflow:
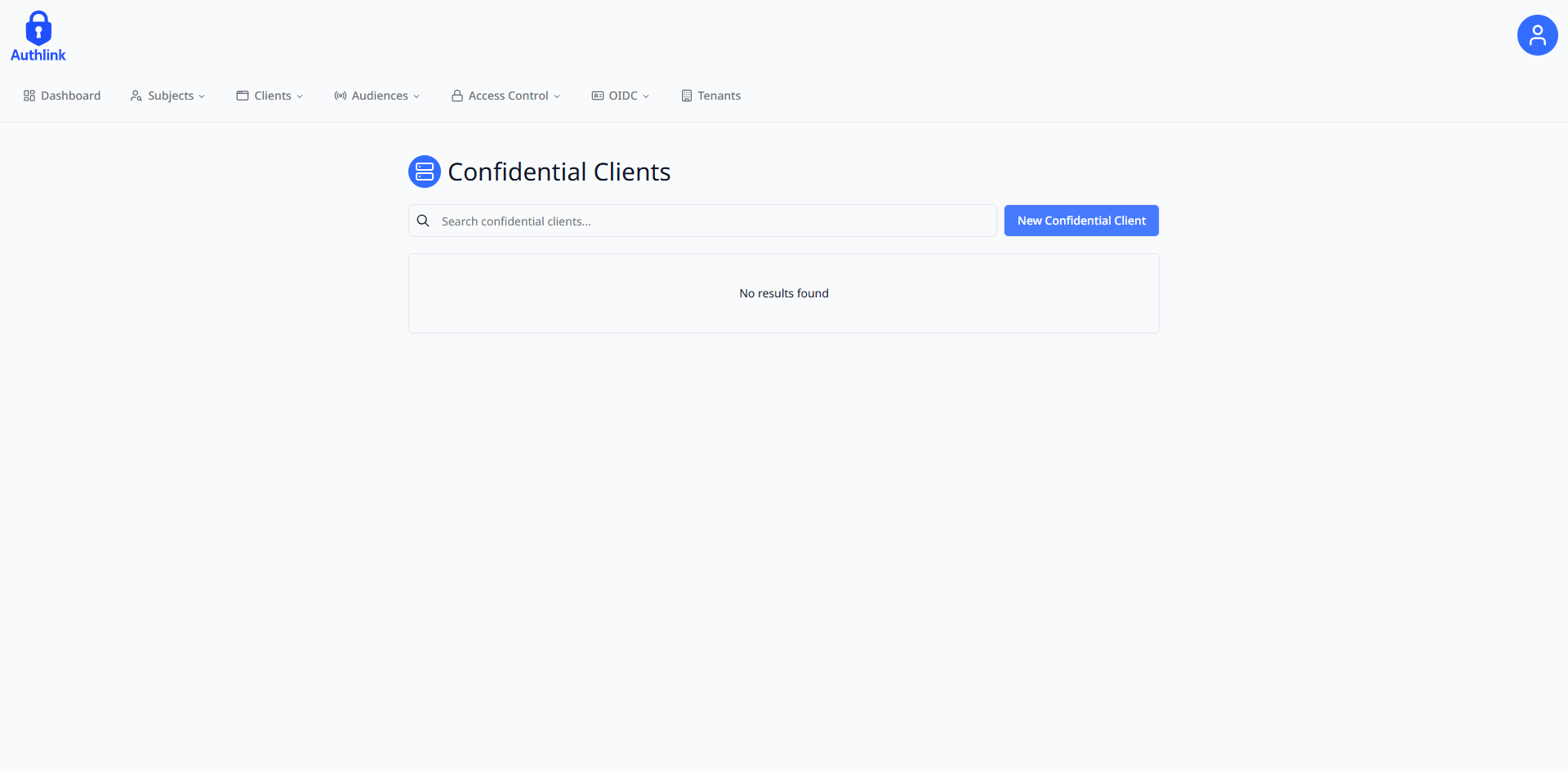 Navigate to https://portal.authlink.co.za/confidential-clients and click on the "New Confidential Client" button
Navigate to https://portal.authlink.co.za/confidential-clients and click on the "New Confidential Client" button
 Fill in the required form fields needed to create a confidential client and submit once finished
Fill in the required form fields needed to create a confidential client and submit once finished
API Management
For developers who need to manage clients programmatically, Authlink provides a comprehensive Portal API that enables automated client management workflows and integration with existing systems.
Authlink Portal API Resource
The Authlink Portal API is a system-defined resource that provides programmatic access to all client management operations available through the web portal. This API resource:
- Always Exists: The Portal API resource is automatically available in every Authlink installation
- Comprehensive Access: Provides complete CRUD operations for clients, credentials, and configurations
- Secure by Design: Requires proper authentication and authorization for all operations
- RESTful Interface: Follows standard REST conventions for predictable integration
Setting Up API Access
To manage clients through the Portal API, you need to establish proper authentication:
1. Create a Confidential Client
First, create a confidential client that will be used for API authentication:
 Navigate to https://portal.authlink.co.za/confidential-clients and click on the "New Confidential Client" button
Navigate to https://portal.authlink.co.za/confidential-clients and click on the "New Confidential Client" button
 Fill in the required form fields needed to create a confidential client and submit once finished
Fill in the required form fields needed to create a confidential client and submit once finished
2. Create Client Secret
After creating a confidential client, you must generate a client secret for secure authentication with the Portal API:
- Security Purpose: The client secret provides cryptographic proof of the client's identity
- Required for Authentication: Confidential clients must use both client ID and client secret for token requests
- Portal API Access: The secret enables secure server-to-server communication with the Portal API
- Secret Management: Store the secret securely as it will only be displayed once during creation
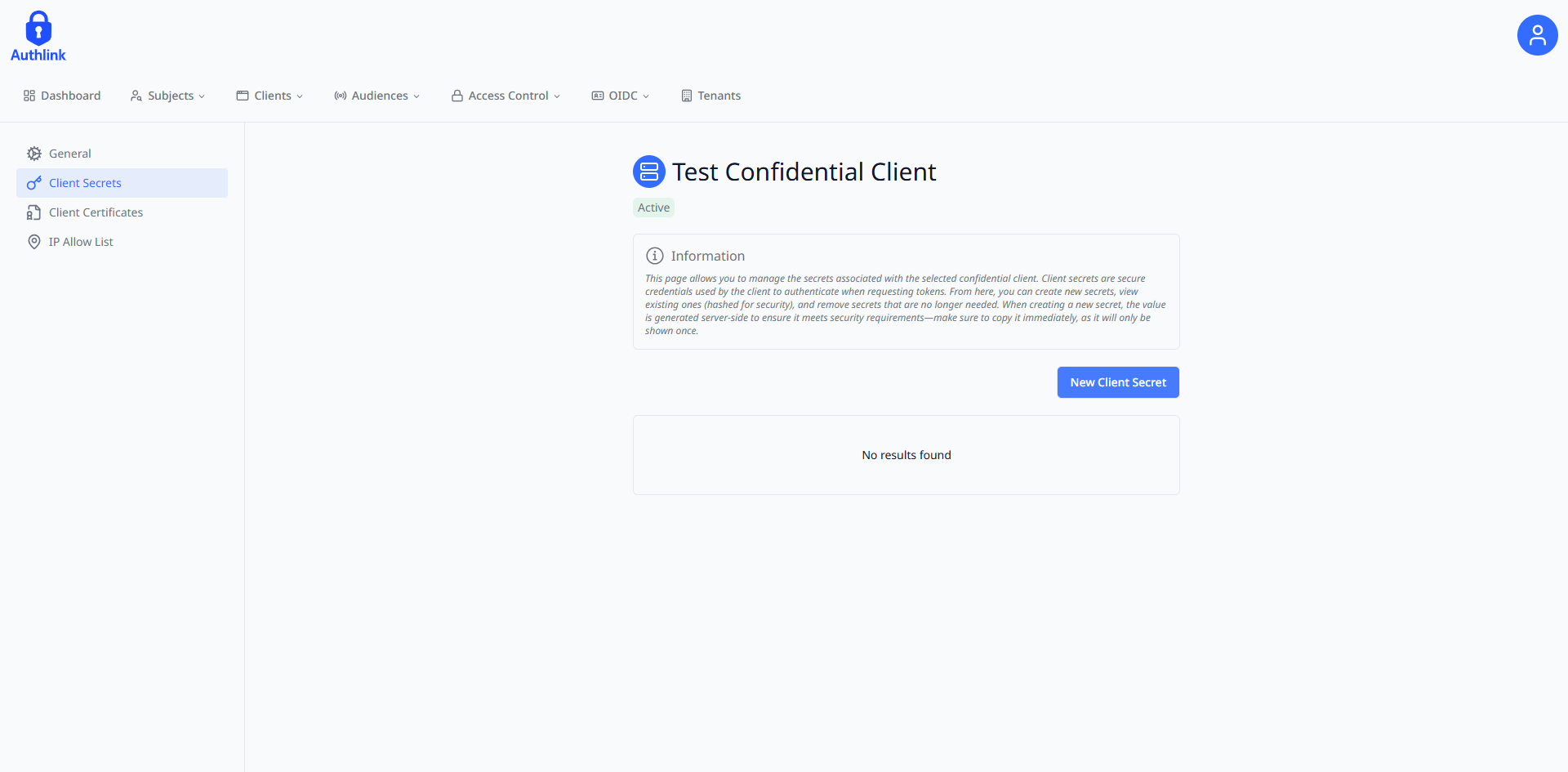 Navigate to the Client Secrets section
Navigate to the Client Secrets section
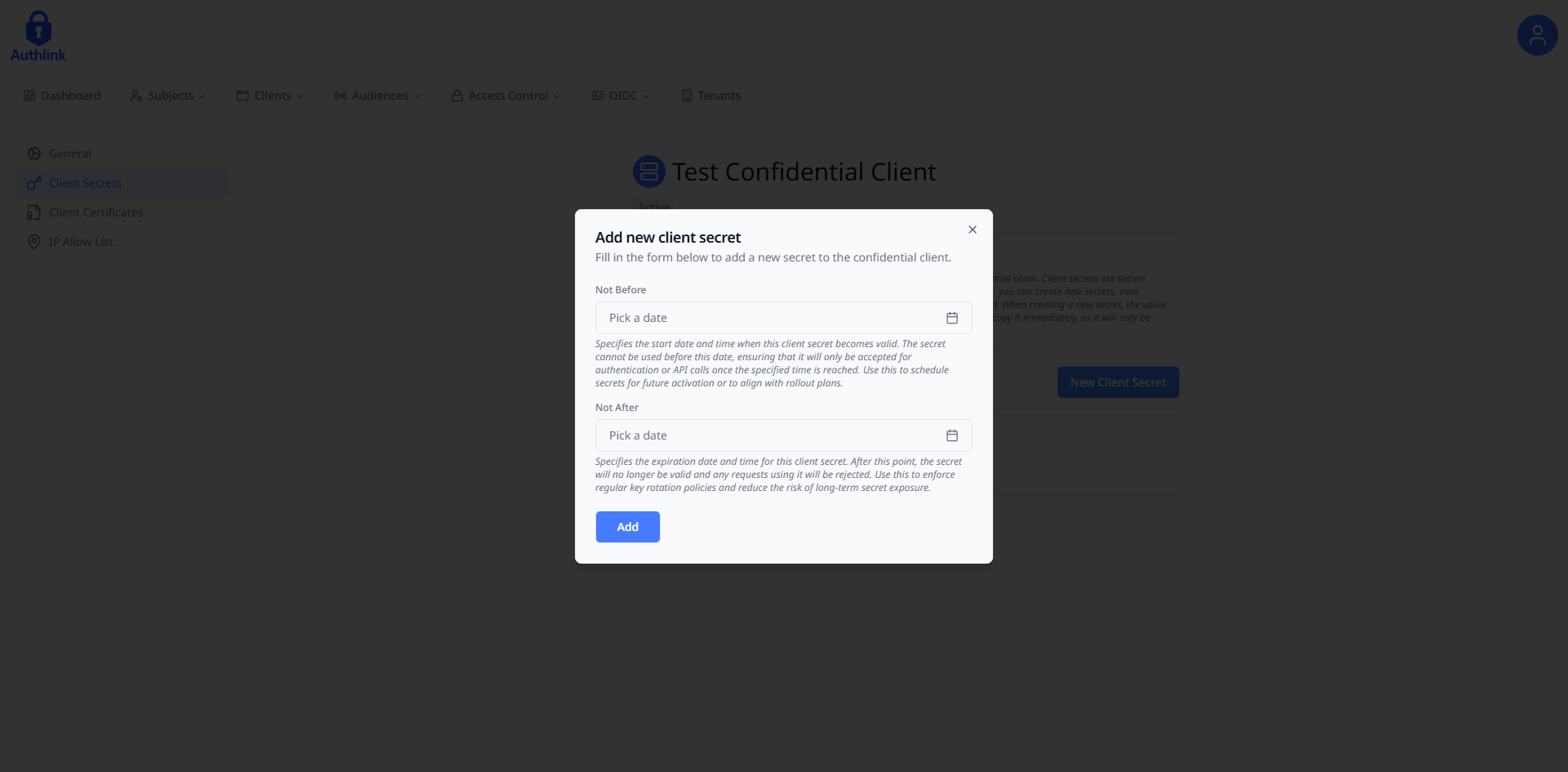 Fill in the required form fields needed to create a client secret and submit once finished
Fill in the required form fields needed to create a client secret and submit once finished
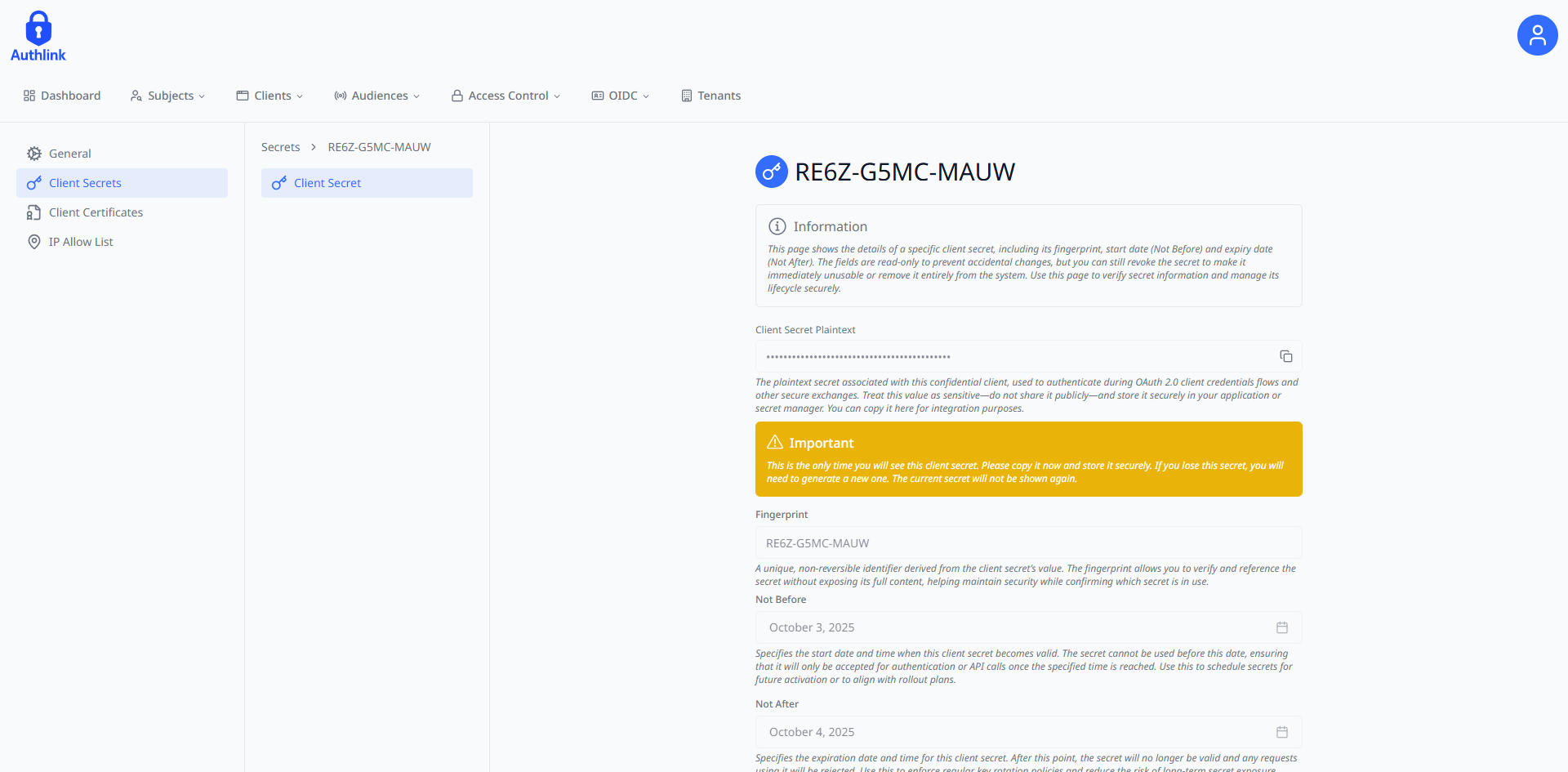 Remember to store the newly generated secret. This will only be available to copy once
Remember to store the newly generated secret. This will only be available to copy once
3. Obtain Access Token
Use the client credentials to obtain an access token:
curl -X POST https://identity.authlink.co.za/api/connect/token \
-H "Content-Type: application/x-www-form-urlencoded" \
-d "grant_type=client_credentials" \
-d "client_id=your_client_id" \
-d "client_secret=your_client_secret" \
-d "scope=roles permissions"API Operations
Once authenticated, your confidential client can perform client management operations:
Client Management Examples:
# Get public clients
curl -X GET https://portal.authlink.co.za/api/public-clients \
-H "Authorization: Bearer your_access_token" \
-H "Content-Type: application/json"
# Get specific public client
curl -X GET https://portal.authlink.co.za/api/public-clients?publicClientId=c28e1647-8aa3-49c5-a8f6-c2027396325b \
-H "Authorization: Bearer your_access_token" \
-H "Content-Type: application/json"
# Create public client
curl -X POST https://portal.authlink.co.za/api/public-clients \
-H "Authorization: Bearer your_access_token" \
-H "Content-Type: application/json" \
-d '{
"name": "Test Public Client",
"description": "Public client for testing purposes.",
"baseUrl": "https://test.example.com"
}'
# Delete public client
curl -X DELETE https://portal.authlink.co.za/api/public-clients \
-H "Authorization: Bearer your_access_token" \
-H "Content-Type: application/json" \
-d '{
"publicClientId": "c28e1647-8aa3-49c5-a8f6-c2027396325b"
}'Best Practices
- Store client credentials securely and never expose them in client-side code
- Implement proper token caching to avoid unnecessary token requests
- Use appropriate scopes to limit API access to required operations only
- Monitor API usage and implement rate limiting for production environments
Understanding client types and their capabilities is crucial for secure integration with Authlink. Next, learn how Audiences define and protect the resources that clients access through comprehensive API Resource management.